XZ Backdoor: What Could Have Been The Biggest Cybersecurity Breach In Recent Times

There was widespread surprise within the cybersecurity and open-source software community last week when news broke out that recent versions, 5.6.0 and 5.6.1 of XZ Utils—a compression tool widely utilised in various Linux distributions—had been found to harbour a backdoor.
In what is currently being described as “the best-executed supply chain attack we’ve seen publicly,” this backdoor, if exploited by individuals possessing a specific private key, could grant unauthorised access to systems and enable them to execute commands with administrative privileges.
Following the revelation of this backdoor, CVE-2024-3094 was assigned to it with a CVSS Score of 10, indicating the severity of the vulnerability.
The Situation So Far
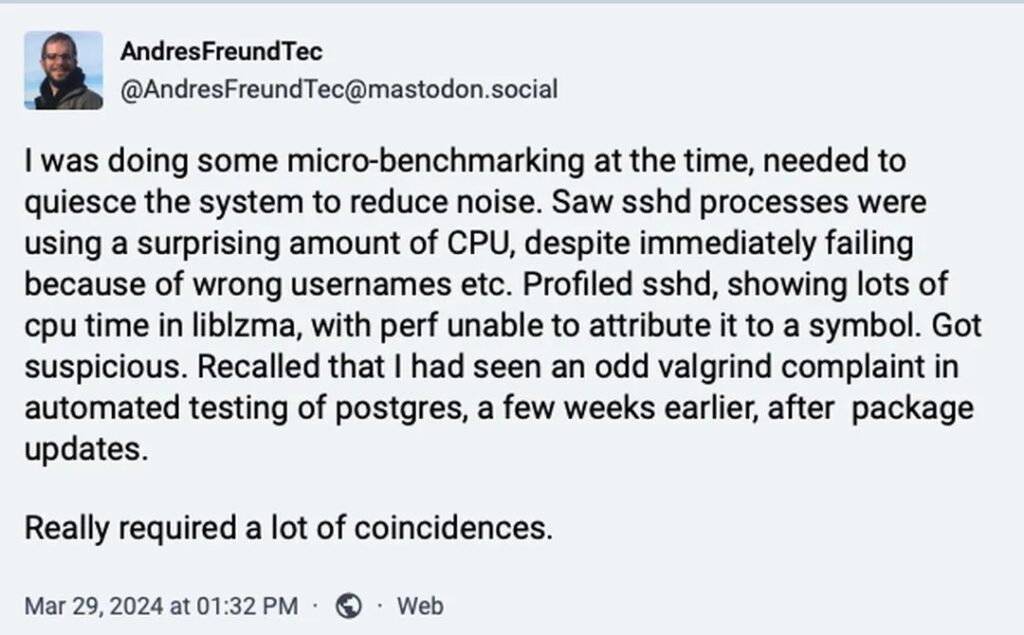
Things fell apart when Andres Freund, a PostgreSQL developer at Microsoft, discovered that the SSH connection on his Linux machine was 500ms slower than expected.
While investigating the issue, Freund, noticed an unusually high CPU utilisation by the sshd process.
Upon further analysis, he traced the problem to excessive CPU time consumed by the liblzma library, a key part of the XZ compression stack, and uncovered the root cause of the issue – the presence of a malicious backdoor planted within the XZ compression library.
On Friday, March 29th, Freund contacted OSS-Security to disclose the updates, foiling the attackers’ two-year plan to exploit the vulnerability on a massive scale.
Freund’s timely action and responsible disclosure helped prevent what could have been one of the most catastrophic cybersecurity breaches in recent history, as the XZ compression library is widely used across a diverse range of software and systems worldwide.
Also Read: Russian Hackers Stole Source Code, Customer Secrets – Microsoft
How We Got Here
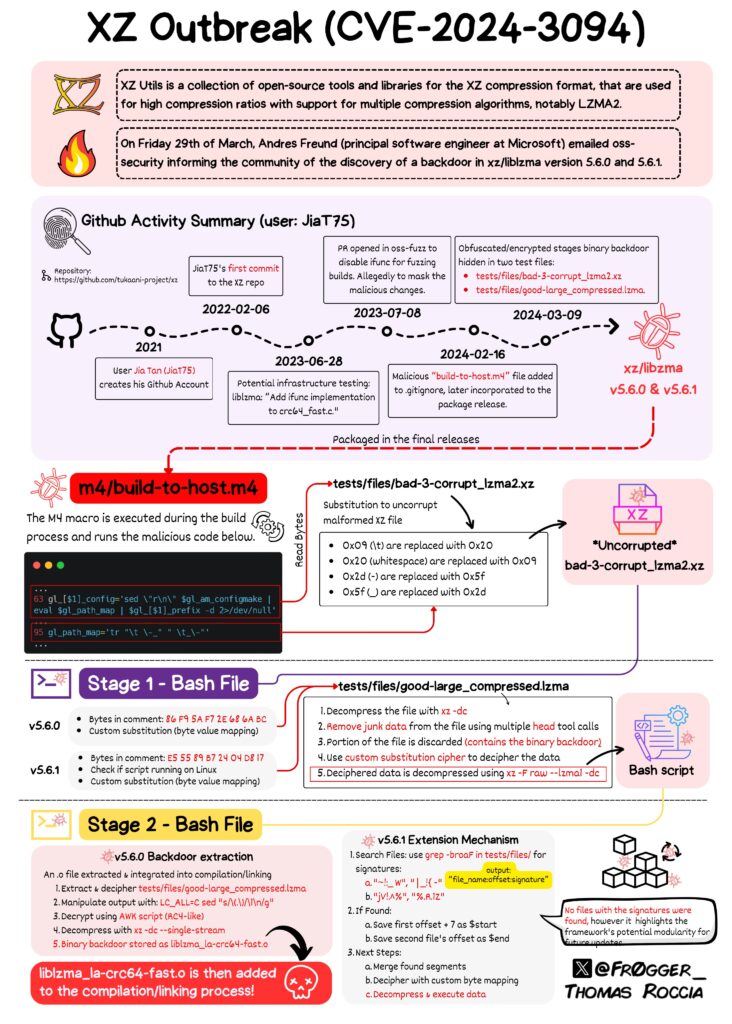
It can be traced back to 2021 when user JiaT75 created their GitHub account and made their initial commit to an open-source project.
The following year, JiaT75 submitted a patch to the XZ Utils mailing list, prompting the sudden appearance of a previously unknown participant named Jigar Kumar.
Kumar wasted no time in criticising the project’s longtime maintainer, Lasse Collin, for not updating the software frequently or quickly enough.
With the backing of several other individuals who had no prior presence on the list, Kumar pressured Collin to bring on an additional developer to help maintain XZ Utils.
The true nature of the threat became clear in January 2023, when JiaT75, now operating under the name Jia Tan, made their first commit to the XZ Utils codebase.
In the ensuing months, Tan’s involvement in the project increased dramatically. They even went so far as to replace Collin’s contact information with their own on oss-fuzz, a project that scans open-source software for exploitable vulnerabilities.
Tan also requested that oss-fuzz disable the ifunc function during testing, a change that effectively prevented the detection of the malicious modifications they were about to introduce.
The coup de grâce came in February of this year when Tan issued commits for versions 5.6.0 and 5.6.1 of XZ Utils, which introduced the backdoor.
In the weeks that followed, Tan or their accomplices actively contacted the developers of Ubuntu, Red Hat, and Debian, urging them to merge the compromised updates into their respective operating systems.
Tragically, one of these malicious updates found its way into several high-profile software releases with multiple Linux distributions, like Fedora, Debian, openSUSE, and Kali Linux, impacted by the backdoor.
Vendors and open-source maintainers are now scrambling to issue updates and security advisories to address the vulnerability.