DNS Encryption: DNS over HTTPS (DoH) and DNS over TLS (DoT)


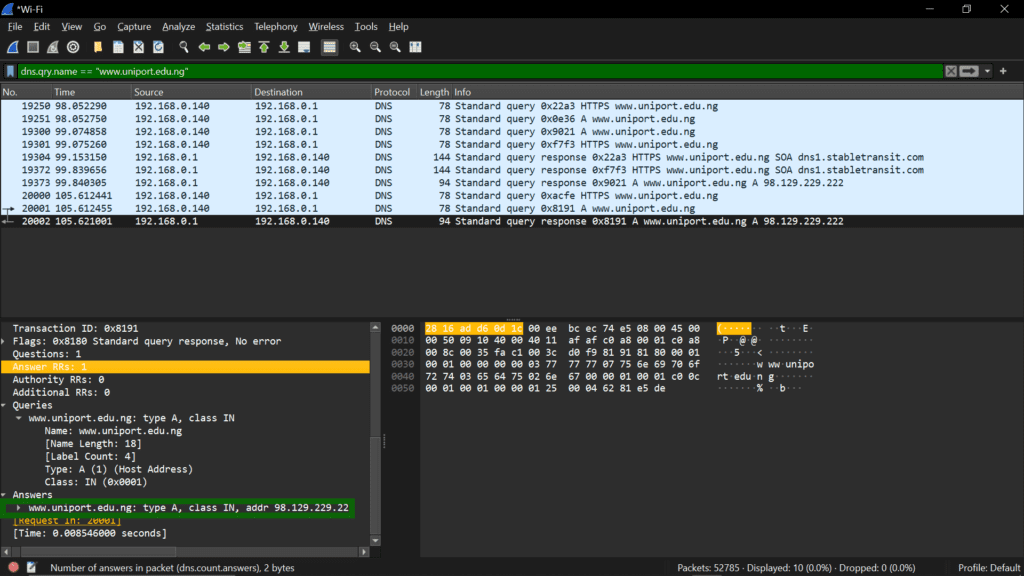
Every time you type a website address into your browser or click on a link, your computer performs a DNS (Domain Name System) lookup behind the scenes.
This lookup translates the human-readable domain name, like “websecuritylab.org”, into the actual IP address that computers use to identify and communicate with the website’s server.
What is DNS and How Does It Work?
When you visit https://websecuritylab.org the following happens:
- Your browser sends a request to a recursive domain name server (DNS) that is configured on your computer. We’ll call this DNS server 1.1.1.1. If you don’t have one configured, you will be routed to your ISP’s DNS server.
- Since 1.1.1.1 does not know the IP address of https://websecuritylab.org , it queries the internet root servers(there are 13 of them), which refer 1.1.1.1 to the nameserver responsible for the .org top-level domain (TLD).
- 1.1.1.1 then asks the .org TLD name server for the authoritative name servers of the websecuritylab.org domain.
- 1.1.1.1 queries the websecuritylab.org name servers for the IP address of the full-quality domain name https://websecuritylab.org. Once the server gets a response, it forwards it to the web browser.
- The browser connects to the IP address and requests the website https://websecuritylab.org.
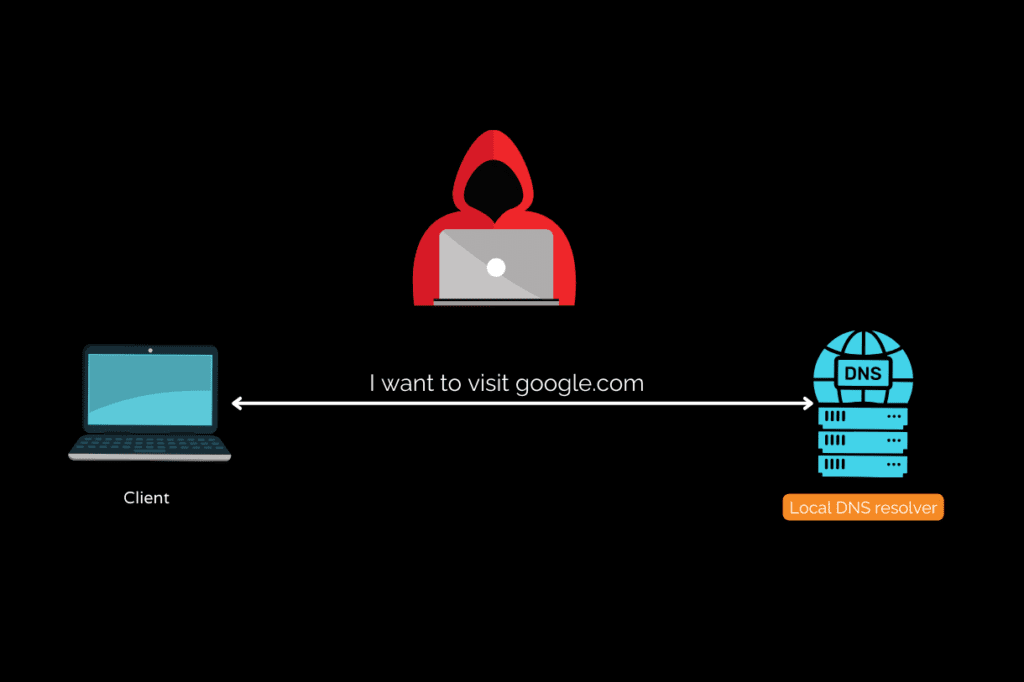
While this DNS process is essential for internet browsing, traditional DNS lookups have a potential privacy and security caveat – they are typically sent over the internet in plaintext, unencrypted form.
This means that any entity monitoring your internet traffic, whether it’s your internet service provider, network admin, or even a malicious actor, can see what websites you are trying to access based on the DNS queries.

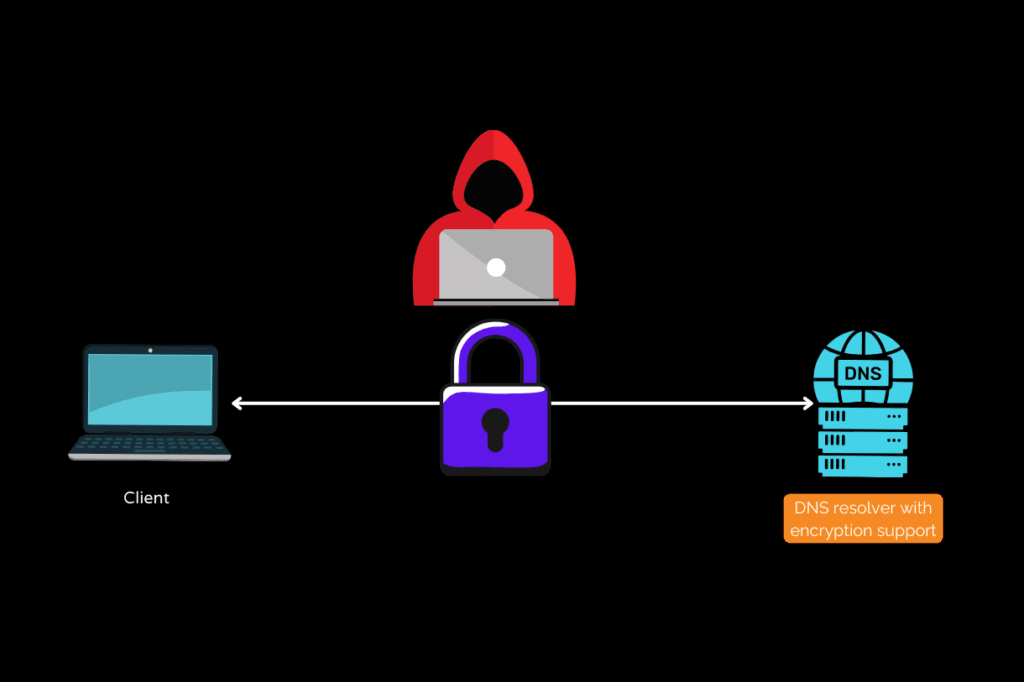
As online privacy and security concerns continue to grow, new protocols like DNS over HTTPS (DoH) and DNS over TLS (DoT) have emerged to address this issue.
DNS encryption aims to safeguard users’ browsing activities by shielding DNS lookups from potential eavesdroppers, including internet service providers (ISPs) and other third parties.
DNS Over HTTPS
DNS over HTTPS (DoH) encrypts DNS queries and responses using the HTTPS protocol, which is the same protocol used for secure web browsing.
It’s an alternative to the traditional DNS protocol (UDP/TCP), which transmits DNS queries and responses in plain text, making them vulnerable to eavesdropping and manipulation.
How DNS over HTTPS (DoH) Works
In DoH, DNS queries and responses are sent over HTTPS, just like regular web traffic.
The client, usually a web browser, sends encrypted DNS queries to a DoH-compatible recursive DNS resolver.
The resolver then decrypts the query, performs the DNS lookup, and sends the encrypted response back to the client over HTTPS.
The HTTPS protocol provides end-to-end encryption and authentication, protecting the privacy and integrity of the DNS communication.
DoH uses the same encryption and security mechanisms as HTTPS, such as TLS/SSL and certificate-based authentication.
DNS Over TLS
DNS over TLS (DoT) is a protocol that encrypts DNS queries and responses using the Transport Layer Security (TLS) protocol.
Like DoH, DoT aims to enhance the privacy and security of DNS communications by preventing eavesdropping and tampering with DNS traffic.
How DNS over TLS (DoT) Works
In DoT, DNS queries and responses are sent over an encrypted TLS session between the client and a DoT-compatible recursive DNS resolver.
The client initiates a TLS handshake with the resolver, and once the TLS session is established, all subsequent DNS queries and responses are encrypted and transmitted over this secure channel.
The TLS protocol provides end-to-end encryption and authentication, ensuring the confidentiality and integrity of the DNS communication.
DoT typically uses TCP as the underlying transport protocol but also supports UDP.
Benefits of DNS Encryption
- Improved Privacy: DoH and DoT encrypt DNS queries and responses, preventing eavesdropping.
- Enhanced Security: DoH and DoT ensure the integrity of DNS communications and prevent tampering or manipulation of DNS responses.
- Censorship circumvention: They can help bypass DNS-based censorship or content filtering.
Potential Drawbacks and Challenges of DNS Encryption
- Centralisation: DNS encryption requires users to trust specific DoH/DoT-compatible recursive DNS resolvers, which could lead to centralisation of DNS resolution and potential censorship or surveillance by the resolver operator.
- Content Filtering: Some organisations, such as enterprises or schools, may find it challenging to implement content filtering or parental controls when DNS queries are encrypted and bypass their local DNS servers.
- Compatibility Issues: DoH and DoT require client and server support, which may lead to compatibility issues with legacy systems or network configurations that are not compatible.
- Increased Overhead: DNS encryption adds overhead, which may result in slightly higher latency than traditional DNS, especially for initial connections or when connection reuse is not possible.
- Firewall and Network Configuration: DoT may require additional firewall and network configuration changes to allow DoT traffic, which can be challenging in some environments, especially those with strict security policies.
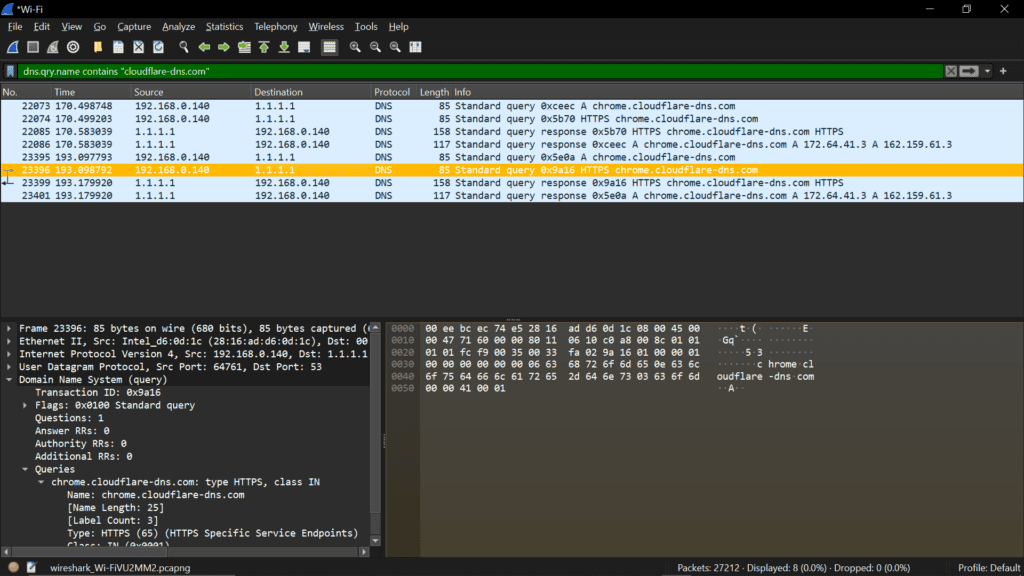
- It Might Not Provide Complete Privacy: Your ISP/network administrator might not be able to see what URL you’re trying to reach, but they can still perform reverse DNS lookups. While reverse DNS lookup is not as easy as it used to be due to the explosion of content delivery networks (CDN) like Cloudflare, it is still very much possible. They can also exploit vulnerabilities in the Server Name Indication (SNI) extension of the TLS protocol. The Server Name Indication (SNI) is a field in the TLS handshake that contains the hostname to which the client wants to connect. This allows the server to present the correct SSL/TLS certificate for that domain. However, the SNI field is sent in plaintext during the initial TLS handshake before the encrypted connection is established. This means that even though the actual content is encrypted with HTTPS, an ISP or other observer can still see the hostname (it is mostly domain name) you are trying to access by inspecting the SNI value. Recently, we have seen a rise in the use of ESNI to mitigate this vulnerability.
Similarities and Differences between DNS over HTTPS and DNS over TLS
| DNS over HTTPS | DNS over TLS | |
| Encryption Protocol | DoH uses the HTTPS protocol (HTTP over TLS/SSL) to encrypt DNS traffic. | DoT uses the TLS protocol directly. |
| Transport Protocol | DoH typically uses TCP as the underlying transport protocol. | DoT can use either TCP or UDP. |
| Port Numbers | 443 | 853 |
Performance Considerations
Latency and Overhead
- Both DNS over HTTPS (DoH) and DNS over TLS (DoT) introduce some latency and overhead due to the encryption process and additional round trips required for establishing secure connections.
- DNS over HTTPS (DoH) may have slightly higher overhead due to the additional HTTPS headers and negotiation.
- DNS over TLS (DoT) may have lower latency for initial connections, as it can use UDP for the first packet exchange.
Caching and Connection Reuse
- DNS over HTTPS (DoH) can benefit from existing HTTPS caching mechanisms and connection reuse in web browsers, which can improve performance for subsequent requests.
- DNS over TLS (DoT) may have more limited caching and connection reuse capabilities, depending on the implementation and the underlying transport protocol (TCP or UDP).
Network and Firewall Considerations
- DNS over HTTPS (DoH) can leverage existing HTTPS infrastructure and may be more easily deployable in environments where HTTP(S) traffic is allowed.
- DNS over TLS (DoT) may require additional firewall and network configuration changes to allow DoT traffic on specific ports.
Setting Up DNS Encryption Using Cloudflare
Cloudflare’s 1.1.1.1 recursive DNS resolver supports DNS over TLS (DoT) and DNS over HTTPS (DoH).
The documentation on how to set it up can be found here.